- Investigate the 4625 (Login Failure) or 4740 (Account Lockout) event itself via a SIEM or in the application EventViewer.
- Press Windows Key + R, type eventvwr, and press Enter
- In Event Viewer, navigate to Windows Logs > Security
- Look for information about the source such as “Calling computer”, “Workstation Name”, or “Source Network Address”
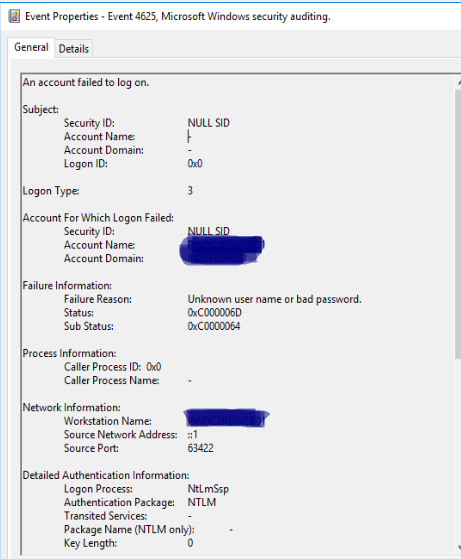
- Take note of a general time range of the login failures. Use one of the fields above and filter with your SIEM or Firewall logs using a time filter around the time of the events – ideally your SIEM with logs including host based running processes and/or Sysmon logs.
- Then take the same search and add filters for one of the source fields above. Review the resulting logs. You should be filtering on time and a source field from above. Be on the look out for running processes.